Shame, Forgiveness and Cyber Risk
I want to highlight, in broad strokes, a divide between how InfoSec and insurance practitioners approach security failures.
InfoSec culture broadly focuses on the failure of victims to implement an idealized security posture. Meanwhile, insurers broadly forgive policyholders for their cybersecurity sins, accepting that failures are inevitable across a large enough portfolio. This is the difference between risk shaming (InfoSec) and risk forgiveness (insurance).
Last week I wrote about one aspect of risk forgiveness—the surprising lack of cyber insurance disputes over the security posture of policyholders.
This led to some interesting discussion on LinkedIn, which I’m embarrassed to say is now my go-to social network. A few insurance practitioners noted that questionnaires and exclusions had become less ambiguous over time. Michael noted that:
“The “Failure to Follow Minimum Required Practices” exclusion you referenced is a provision that is not found in most current cyber insurance policies.”
Anthony Hess suggested that forward thinking insurers had got rid of the question “How many PII records are held on your network?”
But the responses over in InfoSec land were the most interesting. J.J Thompson, a security thought leader, shared the article and interpreted the lack of disputes as a failure, by noting that
“In cyber insurance, the "rules" should be clear, known, communicated up front, and insureds should prove they comply. Then, if there's a claim, you simply re-confirm that at the point of time in which the qualifying event occurred, was the insured doing what they promised. If yes, play the claim.”
I found this to be a strange response. The lack of disputes suggests the “rules” of cyber insurance are clear enough for customers to avoid unpleasant surprises, so what problem are we trying to solve? Why does the insured need to verify they are “doing what they promised”?
In my opinion, this is symptomatic of the wider culture of blame within InfoSec. Mainstream InfoSec says cybersecurity incidents are caused by the organization or individual failing to implement an idealized security posture. Victims of incidents should therefore be punished, either materially or via reputation, for their unreasonable security posture—this logic almost has a moral flavor.
How InfoSec Transfers Risk
You can see the logic most clearly by contrasting how insurers and InfoSec vendors set up risk transfer schemes… yes, some vendors offer risk transfer via cyber warranties, which can be seen in Figure 1 and also my Black Hat 2023 talk. Warranties are essentially insurance policies bolted onto InfoSec service level agreements, often for free if the customer purchases a premium tier solution.
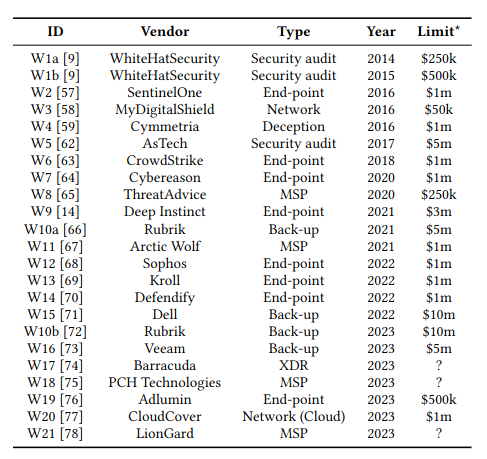
Cyber warranties are typically conditioned on much stricter security requirements than cyber insurance. For example, Rubrik offer a $5 million warranty covering ransomware incidents with the clause:
“Data Security Best Practices. Customer must follow the Rubrik security best practices as defined in the latest version of the Security Hardening Best Practices Guide, which can be found on the Rubrik support portal or provided upon request and includes without limitation the following:
Data Health
• Back-ups are successful and meet the SLA Policies
• Retention lock is enabled for the Customer data in the SLA Policies
User Access
• Multi-factor authentication for all user accounts
• SSH key-based with passphrase protected keys for CLI authentication
• User roles are assigned with least privilege access
Data Encryption
• Data-at-rest and in-transit are always encrypted
• Secure protocols for third-party systems
Application Access
• Create IP whitelisting that limits connections to Customer owned networks only
• SSL-certificate security for User Interface (UI) and APIs
API Security
• Secure service accounts
• Scoped API roles
with least privilege”
This level of prescriptive detail would not be found in a cyber insurance policy.
Given these strict requirements, it is natural to wonder how often cyber warranties pay out on claims (just like we did last week with cyber insurance). Unfortunately, we have even less data than we did last week.
I have one anecdote from the BlackHat vendor area. A sales person at one of the biggest InfoSec vendors proudly claimed that the vendor had never paid out on a warranty. This fact was intended to show how effective their MDR solution was, but really it shows the lack of meaningful risk transfer.
If this anecdote generalizes, then InfoSec vendors always find a basis for denying the claim under the warranty. This fits the moral economy of InfoSec, in which customers who do not implement the ideal security posture are punished.
Risk Pools as Forgiveness
So far we have argued that InfoSec is wired to blame victims of security incidents, which raises the question of what insurers do instead. My answer is that they pool risk and, broadly, forgive customers for their incidents.
Insurers accept that security victimization is stochastic. Attackers pick targets somewhat randomly, employees fall for some phishing emails but not others, and IT environments are in constant flux. A business might deploy a patch the same day as a security advisory for one vuln, and then for another vuln take 2 weeks over the holidays when the head of IT is on maternity leave. Similarly, management might hire a security architect who makes a fundamental oversight because of reasons.
Businesses can hardly control these seemingly random events, but they can smooth the security outcomes. Cyber insurance does not punish businesses for hiring the person in accounts who accidentally fell for a well-crafted funds transfer fraud, nor did it punish businesses for existing during the ransomware epidemic.
2021 is one example of mass forgiveness. Ransomware gangs were rampant, and insurers were paying out a lot in claims. Insurers like AIG and AXIS Capital paid out more in cyber claims than they earned as revenue (see Figure 2).
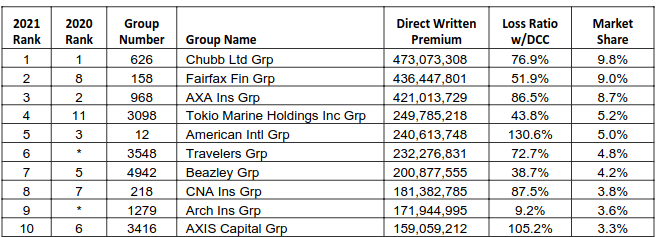
If insurers had a clause like Rubrik’s, they undoubtedly could have found reasons to deny these claims. They did not do so, largely because insurance exists to pay claims, and so security sins are forgiven.
The Right Amount of Forgiveness?
If InfoSec practitioners haven’t already rage closed the article, they will raise the issue of accountability. If we forgive cybersecurity sins, businesses will keep sinning, and cyber crime will continue.
This is the classic story of moral hazard, in which businesses engage in riskier behavior because the risk is transferred to some third-party (e.g. an insurer via insurance or a vendor via a warranty). Moral hazard is an important consideration, and I think the cyber insurance industry has made progress on this, although that’s unevenly spread across providers.
But I actually think the blame vs forgiveness dichotomy has another side. What about whether the blamer/forgiver is held accountable?
Insurers cannot hide from their loss ratios. Individual underwriters are held accountable for selecting bad risks by cyber insurance product leaders. Cyber insurance leaders are held accountable for poor loss rations by the wider company, who might respond by deploying capital to more profitable lines. Another form of accountability comes from reinsurers who increase prices and/or reduce the amount of coverage based on underwriting performance.
Together, these accountability forces led the cyber insurance industry into a re-think. Post 2021, some insurers reduced exposure and even withdrew from writing cyber. Some start-ups failed to raise more funding and were forced to exit via a discounted acquisition etc. This accountability for the risk management providers results from products and a philosophy that forgives customers.
In contrast, the InfoSec industry largely marched through the ransomware epidemic without large-scale recriminations. InfoSec solutions don’t fail, their customers do. This failure could be anything from not buying the right solutions to not configuring solutions properly to not patching quite fast enough. The blame culture doubles up as a form of self-preservation and avoiding accountability.
I don’t think this is the whole story. One positive trend was the mass adoption of Managed Detection and Response. In a sense, MDR is a move towards forgiveness, as the vendor’s increased responsibility reduces the potential routes to blaming the customer. Interestingly, insurers went in the same direction by launching MDR services and offering discounts.
Outlook
Risk management providers (both InfoSec and insurance) need to balance accountability and forgiveness. The optimal balance depends on the customer. Large enterprise companies with teams of security employees need the InfoSec industry’s idealized security posture as a form of accountability. For example, the banking industry invested at scale and has largely (touch wood) weathered the ransomware storm, with some exceptions.
But if InfoSec wants to succeed outside the enterprise market, it will need to embrace forgiveness. It is unsustainable to blame security failures on under-resourced SMEs without a single security employee—those companies need to have their decision burden reduced. One direction is to make solutions secure by design, another is for the vendor to manage the solution, and another is customer support and education.
Both insurers and InfoSec vendors need to discover a business model that forgives security failures while simultaneously improving security. I think insurance with free security services is one such model (which I’ll explore in the future) but I am yet to see what the InfoSec version is.